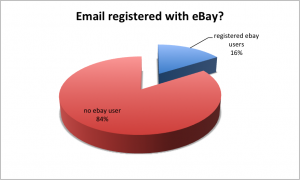
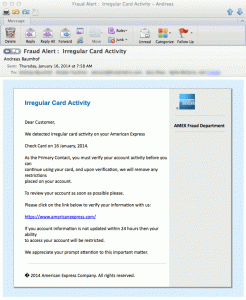
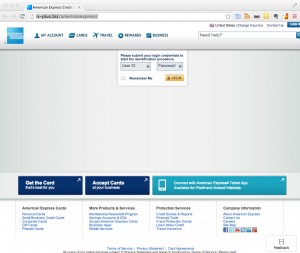
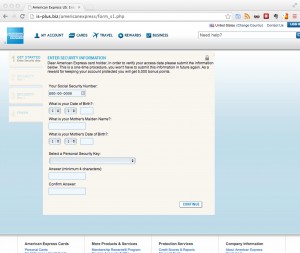
I came across this blog post (locally cached pdf) a couple of days ago of a developer of a Chrome extension who filled the gap after Google dropped support for the RSS reader. His Chrome extension was popular and gained more than 30,000 users.
To cut the long story short, he sold it for a 4 figure amount to someone who then turn his extension into a adware riddled version and updated all 30,000 users.
That seems to be an awful efficient way of infecting a lot of users for very little money. His chrome extension was “Add to Feedly”.
Unfortunately these things occur more and more often. Another example is “Tweet this Page” was taken down by Google due to it starting to hijack google searches. Apparently the developer sold it for $500! (from here)
In both cases, the bad guys talked the authors into selling by making nice claims such as “…they wanted the extension ‘for further development’”.
The funny thing is that Google (who is distributing Chrome) is making around 97% of its revenue from online ads, so it is not surprising that advertising within chrome extensions is neither prohibited nor discouraged.
“…Injected ads are allowed in Chrome extensions, but Google’s policy states that which app the ads are coming from must be clearly disclosed to the user, and they cannot interfere with any native ads or the functionality of the website.” (from here)
For malware authors, hijacking legitimate and good extensions is an outstanding business model. First of all, they know exactly how many potential victims they can buy. Secondly, due to auto-updates they can infect these people nicely and thirdly it takes quite a while for google to remove “non-behaving” extensions from the store.
What is the risk here? or What can a malicious chrome extension do?
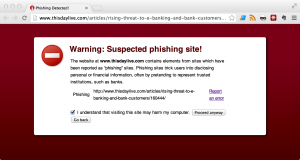
Google has automated screening capabilities that will minimize the distribution of malware through chrome extensions. However we all know that malicious actors have tools available to make sure their software is never be found to be malicious. But then again, launching an executable (malicious or not) in a completely transparent way is not so easy.
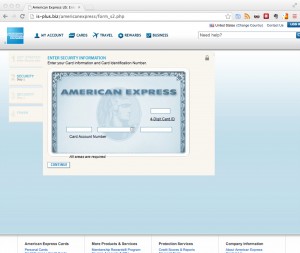
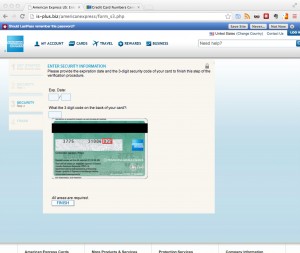
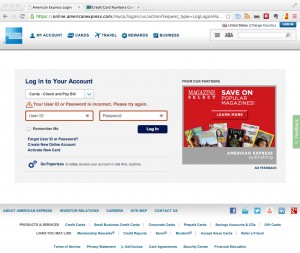
The much bigger risk is that the chrome extension has full control of the website content, including all form fields. This could mean that a malicious chrome extension can
- inject any kind of javascript into the website, effectively providing the same functionality as every sophisticated banking trojan out there. Should we call this Zeus-in-the-Extensions

- sniff any provided input values into form fields. These could be usernames, password, one-time-password, tokens, email addresses, date of birth, SSN and much more.
Google has already announced that their extension policy is due to change in June 2014 and the new policy will require extensions to serve a single purpose. It would never cross my mind that they do this to vastly increase the number of chrome extensions, but surely only to provide a good service to us.
Oh, they also make it easier to use payment options to extensions. I can already see the topic for a future blog post.