I’ve seen a “nice” spam campaign that was very successful from my point of view…
- First of all, I received this email to my corporate account which passed all of our AV/spam and other filters.
- That email looked actually not too bad (a bit generic, but voicemail systems are this way

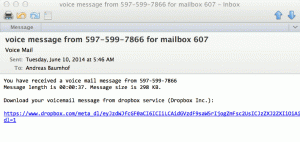
- The interesting fact was that the link goes to dropbox – which is more and more making an inroad into corporate businesses.
- The link therefore doesn’t raise any suspicion. It is even served “securely” (read “encrypted”) via https://…
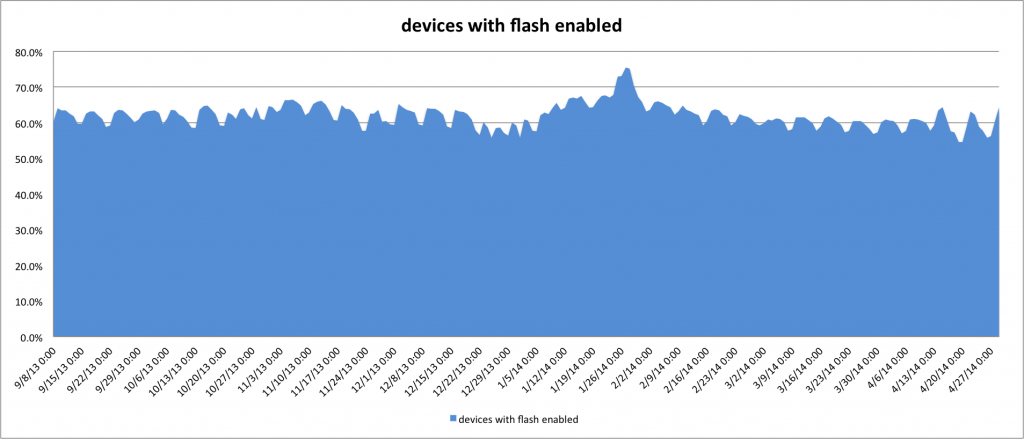
- Even though our gateway based virus scanner failed to detect it, 13 out of 52 AV engines as part of Virustotal detected it: https://www.virustotal.com/en/file/7637d5df5ce0e300a8a56ccefa37e49228517e8797aecfe439b32a14750de0b8/analysis/
- I have to say that Dropbox reacted very quickly and took down the link within hours.
The source of the email is listed below…
... some lines removed ... Received: from X-Virus-Scan: V- X-Note: Spam Tests Failed: X-Country-Path: INDIA->UNITED STATES X-Note-Sending-IP: 180.215.31.112 X-Note-Reverse-DNS: X-Note-Return-Path: countable842@rocajunyent.com X-Note: User Rule Hits: X-Note: Global Rule Hits: G327 G328 G329 G330 G334 G335 G346 G445 X-Note: Encrypt Rule Hits: X-Note: Mail Class: ALLOWEDSENDER X-Note: Headers Injected Received: ...removed... with ESMTP id 207187012; Tue, 10 Jun 2014 07:43:15 -0500 Message-ID: <SX5HTCQD.0875474@rocajunyent.com> Date: Tue, 10 Jun 2014 18:16:17 +0530 From: Voice Mail <voicemail_sender@...removed....com> User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101 Thunderbird/24.2.0 MIME-Version: 1.0 To: <abaumhof@...removed....com> Subject: voice message from 597-599-7866 for mailbox 607 Return-Path: countable842@rocajunyent.com Content-type: text/plain; charset="US-ASCII" Content-transfer-encoding: 7bit You have received a voice mail message from 597-599-7866 Message length is 00:00:37. Message size is 298 KB. Download your voicemail message from dropbox service (Dropbox Inc.): https://www.dropbox.com/meta_dl/eyJzdWJfcGF0aCI6ICIiLCAidGVzdF9saW5r IjogZmFsc2UsICJzZXJ2ZXIiOiAiZGwuZHJvcGJveHVzZXJjb250ZW50LmNvbSIsICJpdGVtX2lk IjogbnVsbCwgImlzX2RpciI6IGZhbHNlLCAidGtleSI6ICIxeWEwMGx3enQ1aWdpOXEifQ/AANAB ss7_JqczoocZG5p_SjA659fq_BNbEs6hyC4CqDuBA?dl=1