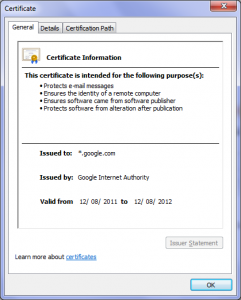
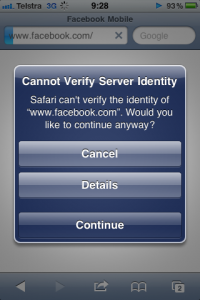
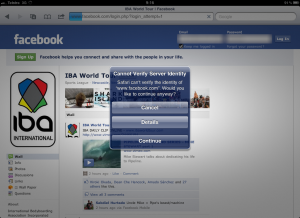
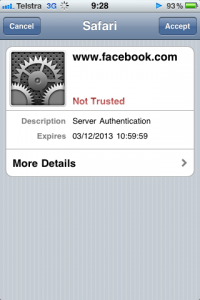
Brian Krebs published some stats from ThreatMetrix around how quickly users upgrade their browsers once security incidents have been posted. See http://krebsonsecurity.com/2014/05/the-mad-mad-dash-to-update-flash/ for more details.
I have read bits and pieces but the economic impact of having security incidents is a very interesting topic and I think it ranges from breaches/security incidents having zero impact on the business (apart from a temporary drop) and businesses going out of business due to that (Diginotar is an example - http://www.darkreading.com/attacks-breaches/diginotar-hacked-out-of-business/d/d-id/1136356?, or Target’s Ex-CEO as well)
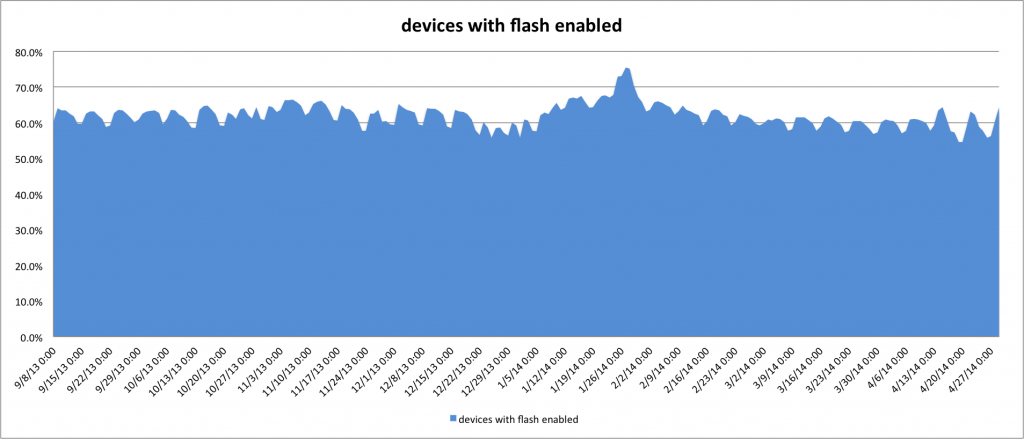
Concluding the data analytics exercise with Flash, the below chart shows the number of devices flash is installed. The data looks at all of the endusers of our 2,500 enterprise customers of ThreatMetrix’s Global Trust Intelligence network representing more than 160 million accounts.
As you can see that the percentage of flash is very constant at around 62% of the devices and not a single one of Adobe’s security critical severity incident over the last 6 months encouraged enough people to stop using Adobe Flash.
My personal advise: If you haven’t uninstalled Flash, do it now.