We have posted some technical analysis to the mebroot/MBR/Sinowal trojan lately and while we at TrustDefender Labs focus quite heavily on the analysis of the trojans and infection vectors itsself on the client side, Researchers at the University of California looked at the data they received on the server side. This compliments our research quite nicely as it provides hard facts how successful those attacks are and how much data the bad guys actually receive.
The research was done by Researchers at the Security Group, Department of Computer Science at University of California, Santa Barbara released a very interesting paper “Your botnet is my Botnet: Analysis of a Botnet Takeover”. (see http://www.cs.ucsb.edu/~seclab/projects/torpig/index.html)
In this paper the security researchers “infiltrated” the Torpig C&C control network for a period of 10 days and their results are nothing less but astonishing.
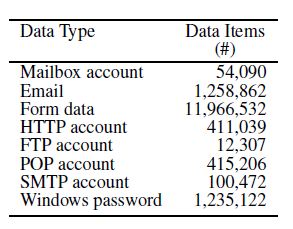
In the 10 days, the sinkholed C&C Server collected almost 70GB of data. This data included stolen credentials from 52,540 different infected machines and they sent some 297,962 unique credentials (username/password), credentials of 8,310 bank accounts at 410 different financial institutions. Furthermore the data included more than 11 million HTTP(S) Form Data, 1,258,862 email accounts, 1,235,122 windows password, …
Key quotes by the original text are:
The top targeted institutions were PayPal (1,770 accounts), Poste Italiane (765), Capital One (314), E*Trade (304), and Chase (217).
The most common cards include Visa (1,056), Master-
Card (447), American Express (81), Maestro (36), and Discover
(24).
While 86% of the victims contributed only a single card number,
others offered a few more. Of particular interest is the case of a
single victim from whom 30 credit card numbers were extracted.
Upon manual examination, we discovered that the victim was an
agent for an at-home, distributed call center. It seems that the card numbers were those of customers of the company that the agent was working for, and they were being entered into the call center’s central database for order processing.
And very interestingly they also looked at the financial implications of this
Quantifying the value of the financial information stolen by Torpig is an uncertain process because of the characteristics of the underground markets where it may end up being traded. A report by Symantec [37] indicated (loose) ranges of prices for common goods and, in particular, priced credit cards between $0.10–$25 and bank accounts from $10–$1,000.
If these figures are accurate, in ten days of activity, the Torpig controllers may have profited anywhere between $83k and $8.3M.
Also, a Torpig server was seized in 2008, resulting
in the recovery of 250,000 stolen credit and debit cards and 300,000 online bank account login credentials [31].
For more on the botnet hijack, check out UC Santa Barbara’s Torpig project page. Also features on Slashdot.
