1 Executive Summary
We at TrustDefender Labs have been analysing various transactional Trojans for quite a while, and lately Zeus has been at the top of the class with a massive feature-set and a massive distribution network. Why create a new Trojan if the existing ones are still highly effective?
Well, it seems that there are more and more new players entering the scene, and today we will look at one of the new players in great detail, the very “promising” challenger called Carberp.
This Trojan stands for a new class of Trojans that emerged out of an era of highly successful transactional Trojans such as Zeus, Mebroot and Silentbanker.
Carberp shows an impressive series of evolutionary steps to where it is today with a number of highly interesting features that include
- Ability to run as non-administrator
- Ability to infect Windows XP , Windows Vista and Windows 7
- Will not make any changes to the registry (only in memory modifications)
- Sophisticated browser hooking to fully control all internet traffic (including HTTPS with EV-SSL)
- Stolen data is transmitted in real-time to C&C server
We found another fact more interesting from a positioning point of view. It seems that the malware writers are well aware that competing malware is infecting the same computers[1] and we observe a new trend of disabling not just Antivirus engines, but also other Trojans. They will try to disable them to make sure that they don’t interfere (and obviously that the valuable stolen information is not sent to the “competition”).
This Trojan already has a quite impressive feature-set and if it evolves at the same speed as previous Trojans it definitely has the potential to be in the same league as Zeus. But keep in mind that threats only evolve as much as they have to and as security researchers we are always on the lookout for the next greatest technical advancements, but what we learn out from the field is that even phishing is still working fine if used properly.
This Trojan seems to be purpose built and has evolved to where it is today. We anticipate that Carberp will further develop and could morph into a big threat. Hopefully I’ll be proven wrong here but it seems that the bad guys are everywhere and innovating very quickly.
[Update] We will not look specifically into the transactional, HTML overlay techniques this trojan provides similarly to Zeus, Spyeye, Gozi, … as we will cover this in a separate in-depth report.
2 Introduction
We looked mainly at the sample with MD5 07d3fbb124ff39bd5c1045599f719e36 which we obtained from on Wed, Sept 29, 2010. It had a Virustotal detection of 21/41 on the 29th (http://www.virustotal.com/file-scan/report.html?id=61f97c771822ea8c2de0c328d4887febe3fae289e80a0b6caf7768742ae2240f-1285773812).
The sample is packed with ASPack and even though it was a decent detection (well, we consider 51% detection a decent detection), at least four out of the big 6 Antivirus Engines didn’t pick it up.
Furthermore most of the detections were generic ones as this sample was packed with ASPack. Actually only two had a non-generic detection (4.8%).
A static analysis by Threatexpert helps us determining what it is doing on a high level (http://www.threatexpert.com/report.aspx?md5=07d3fbb124ff39bd5c1045599f719e36)
2.1 Additional samples
In addition to the sample above, we looked at the following Carberp samples that date back to June 2010.
- MD5: a4bb486727b5954669da40b5b624fcd4, first seen June 20, 2010
- MD5: 31a4bc4e9a431d91dc0b368f4a76ee85, first seen Aug 3, 2010
- MD5: 171fe667e37132a8b614df0da80b754f, first seen Sep 21, 2010
- MD5: 9209bcea94e4dc160587e64600a1297b, first seen Sep 25, 2010
However these samples did not provide the three plugins mentioned later on in this report, but just a single “grabber” plugin
2 Confusion in regards to the naming of Carberp
There seems to be quite a bit of confusion within the Antivirus community in determining what Carberp is or is not. While doing our research, we have come across a number of samples where at least one Antivirus Engine detects Carberp while the sample is either Zeus or something completely different.
We have learned already in the previous chapter that it is not yet a well-known Trojan and many Antivirus Engines only detect it using heuristics (which will give you very cryptic names).
more details in the in-depth report.
3 Role of geographic IP
It is quite common these days that distribution and execution of Trojans are very heavily geographic based. Based on the client IP address, the C&C servers will determine whether to infect a system at all or how to behave. We have seen geographic detection tools quite heavily for Mebroot and also Zeus.
While we haven’t noticed a different behaviour based on the geographic location, we received the following error message while doing some research. GeoIPCity.dat was a free geographic database provided by Mastermind.
4 Internet Requests
After installation, Carberp will automatically make a few requests to the internet to download additional files.
Our sample had a hard-coded C&C server at <<<HOST>>> which according to whois.sc is registered in March 2010 (!).
For more details please refer to the in-depth report.
4.1 1st request: Transmission of a unique ID
The first internet request will transmit a unique ID of the computer to the C&C server (POST /set/task.html with id)
After that, the id will always be used for any transmissions to the C&C server.
4.2 2nd request: Upload of all running processes
The next request is an upload of all running processes. Carberp performs a POST request to /set/first.html with the following parameters (this might differ from computer to computer)
- <<NUMBER>>&os=Windows XP Service Pack 3&plist=system,smss.exe,csrss.exe,winlogon.exe,services.exe,lsass.exe,vmacthlp.exe,svchost.exe,svchost.exe,msmpeng.exe,svchost.exe,svchost.exe,svchost.exe,spoolsv.exe,svchost.exe,vmtoolsd.exe,explorer.exe,vmupgradehelper.exe,vmwaretray.exe,vmwareuser.exe,msseces.exe,ctfmon.exe,alg.exe,wscntfy.exe,wuauclt.exe,procmon.exe,wmiprvse.exe,wireshark.exe,dumpcap.exe,svchost.exe,svchost.exe
4.3 3rd request: Download of additional binary files
Immediately after that, Carberp will additionally download three more files
- GET /cfg/passw.plug HTTP/1.1
- Size: 681,835
- MD5: 21ca03e809a418abc36a32630ac62b73
- GET /cfg/miniav.plug HTTP/1.1
- Size: 581,200
- MD5: a041b68ce03e4918706ce3837c3c4e56
- Get /cfg/stopav.plug HTTP/1.1
- Size: 487,035
- MD5: 8d761ecbae90de25d5165d8aac4fb585
We will look at these file in more detail later on in this report.
5 Installation
After execution, Carberp will create a number of temporary files in the %TEMP% directory (c:documents and settings<USER>Local SettingsTemp on Windows XP) or c:users<USER>AppDataLocalTemp).
Carberp does not need to have administrator rights to run and operate, in fact the Trojan is very careful not to create any files or use anything so that it would need administrator privileges.
While this very disturbing fact means that the Trojan will natively run on locked down machines, as well as on Windows Vista and Windows 7, it also means that the Trojan will only infect the currently logged on user. It will not infect any other user or any kernel component of the system at all.
It follows a similar approach as the Zeus Trojan where it is much more important to spread the Trojan on the newer Windows Operating Systems and this is very disturbing news.
On our system, Carberp created the following files
- %temp%F.tmp
- %temp%/10.tmp
- %temp%/11.tmp
- %temp%/~TM12.tmp
- %temp%/~TM13.tmp
- %temp%/14.tmp
5.1 Execution
Available in the in-depth report
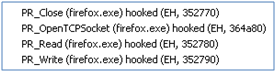
6 Windows / Browser Hooks
Carberp will hook the Export table of a number of WININET.dll and USER32.dll functions. The most important ones being
- WININET.dll
- InternetReadFile
- InternetCloseHandle
- HttpSendRequestA/W
- InternetReadFileExA/W
- HttpSendRequestExA/W
More details available in the in-depth report.
7 Hidden files (for activation after restart)
As the Trojan won’t make any permanent changes to the system, Carberp needs to make sure that it is re-activated after a system restart.
It is performing this task by copying itself to the Startup section of the currently logged on user (c:documents and settings<USER>Start MenuProgramsStartup) with chkntfs.exe in our case. The MD5 is exactly the same as the initial dropper itself.
However the file is hidden from the operating system and you won’t find it with the Windows Explorer or even with the command line. Even the “old” tab-complete trick doesn’t work and this file is really completely invisible.
Special tools such as GMER can make it visible
8 Internet traffic interception (stealing of real-time data)
As discussed before, Carberp has full visibility and control over any internet transactions and it will send off every single password, one-time-token, … for every single login in real-time. It is one of these new Trojans that won’t just collect the data and use it much later, it will send the information out of the computer before it is sent to the real recipient (e.g. our bank).
More details in the in-depth report
9 Detection
This Trojan is very hard to detect without external tools… Obviously TrustDefender detects and protects against it straight out of the box.
The best way to spot a detection is to use the process explorer from Microsoft’s Sysinternals tools (www.sysinternals.com).
Once you start procexp.exe, click on the explorer.exe process and select “View” from the menu and choose “Show Lower Pane”.
At the end of the list, in the “Thread” section, check to see whether there are any threads in a <non-existent Process>. If yes, you are infected. If no, you should be ok from Carberp.
10 Downloaded modules (miniav.plug, passw.plug, stopav.plug)
While we still analyse and work through these downloaded components, we have seen two of these plugins before and they were designed to disable current Antivirus Protection (stopav.plug) and check for the existence of other trojans (miniav.plug). We have seen detection routines for Zeus and Limbo.
While we are still working on the details, this highlights an interesting approach that the Trojan writers are using. They know that if they can compromise a computer, chances might be high that there is already another Trojan running on this machine and they want to make sure that
- multiple different Trojans do not interfere with each other
- the same stolen credentials will not be sent to multiple C&C servers as this would decrease the value and the uniqueness of the data.
11 Appendix: How does TrustDefender deal with it?
The TrustDefender Agent will fully detect and protect against Carberp in various ways straight out of the box. TrustDefender doesn’t need signatures or pattern updates and our online transaction security solution was designed to protect the user and the financial institution right from the start.
More information can be found in the in-depth report or please contact us at info@trustdefender.com
[1] well, if you didn’t care about your security, chances are high that you get infected multiple times