 Introduction
Introduction
Well, here we are again… After the gang behind Zeus released a new major release of the Zeus Trojan (dubbed Zeus v2), it has received quite a bit of media attention. Our report provides an in-depth look at this new threat from a technical level to provide interested parties detailed information what Zeus v2 does and how it performs its dirty tasks.
Although we have covered the Zeus Trojan in the past, we are once again amazed by the innovation and the effort the bad guys have put in place to keep ahead of traditional security initiatives that do not involve the user’s desktop.
These “advancements” can be grouped into two broad categories; development of the core Zeus platform (Trojan and backend) and development of additional functionalities (such as an instant messaging notification capacity and an extensive JavaScript engine for dynamic challenge/response harvesting and real-time activities).
Although both of these categories are equally disturbing, this post will focus on advancements of the Zeus Trojan core platform that have enabled Zeus to target Firefox users as well as run on newer operating systems that have extensive security features inbuilt into them to make life for such Trojans much harder, namely Windows Vista and Windows 7.
These inbuilt hardening features are a result of Microsoft’s development over the past few years in a response to the proliferation of such Trojans targeting their operating systems and browser. We just hope that other vendors are as equally prepared as the bad guys start turning their attention to them with new variants of the respective Trojans.
In addition, these advancements clearly show how the bad guys are willing to adopt new strategies in response to market trends. The more success Firefox has, the more of a target it is going to be. A recent study noted that the market share of Internet Explorer had fallen below 60%[1], and since then we have seen the bad guys trying to increase their market share by targeting Firefox.
Although we have previously seen custom built Zeus Trojans that have such enhancements enabled, these features are now in the core Zeus binary with “official” support and maintenance. This means that these previously custom features are now available to everybody and we believe there will be a big surge of Zeus activity as a result.
In the next part of the Zeus in-depth reports we will look more closely at the “additional” features of Zeus, namely advanced configuration file options and the extensive JavaScript engine for dynamic challenge/response harvesting and real-time activities.
This blog contains some information available in our in-depth report that is available on request by sending an email to labs@trustdefender.com.
SOCKS proxy
Installation
Upon installation on Windows XP, we noticed that we did get a warning from the operating system, as depicted below:
This is the default dialog if a program wants to listen and accept connections on the computer; however we haven’t seen this dialog even with previous Zeus variants as they were running as administrators where it was possible to get around this notification.
The interesting thing here is that Windows is asking the user to unblock the Windows Explorer program. There is no reference to any third-party software or anything suspicious, thus making this confirmation actually look fairly legitimate.
On Windows Vista and Windows 7, you’ll experience the same confirmation but it looks slightly different:
But once again, a legitimate Windows process (taskhost.exe) is asking to be allowed by the user!!!
The “funny” thing is that in the case of Zeus v2 running as administrator, there is no need for this security alert when using the built-in Windows Firewall as the Windows Firewall is probably the only firewall in the world where you can programmatically allow any program (see the fairly undocumented Windows API WindowsFirewallAddApp).
Functionality
The above dialog is produced by Windows as the Zeus v2 Trojan tries to listen and accept connections from the computer. In all of our samples, this port was port 13851 as per the screenshot below and Zeus v2 operates a SOCKS proxy on this port.
This SOCKS proxy allows the bad guys to relay any internet requests through the victim’s computer, which in turn means that any internet requests that the bad guys execute will show up as if it would have been done by the victim. So any passive fingerprinting technologies employed by the web service provider will always see the correct public IP address (and thus the corresponding geographic lookup). This is in use by many risk engines for web authentication.
The SOCKS proxy has another advantage: The bad guys can relay any TCP and UDP traffic through the victim’s machine.
However please note that this SOCKS feature is not new, however obviously we haven’t seen this feature in active on non-administrator accounts! And on Windows Vista and Windows 7, there is actually a big chance that users will allow this as the warning mentions that a legitimate Windows component needs permission to run!!! This is definitely new.
Initial Handshake, Configuration file
See the in-depth report
Firefox Hooking
As mentioned above, this Zeus variant is capable of compromising Firefox in exactly the same way it compromises Internet Explorer. As a result, you will find that a Zeus infected system will have quite a few “hooks” of legitimate Windows functions internally.
These “hooks” mean that the Zeus Trojan is making sure that when Firefox calls HttpSendRequest, the call does not go directly to the Windows API, but rather via the Zeus Trojan before going to the Windows API. In doing this, Zeus has full control over the HTTP and HTTPS sessions made by the Firefox browser.
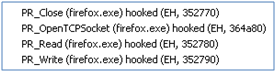
GMER and other rootkit hooking tools detect the following hooks into the Firefox browser.
However the interesting thing is that GMER and other rootkit tools seem to miss a few hooks as these functions are not really used by Firefox. The above functions are from WININET.dll and Firefox uses its own API to connect to the Internet. It also uses OpenSSL for SSL encryption/decryption and all these functions are wrapped in nspr4.dll (which resides in the Firefox program folder).
For an overview of how these are used, please refer to the Mozilla documentation at: http://www.mozilla.org/projects/security/pki/nss/ref/ssl/sslintro.html
If we look more closely, we can see the key functions that are hooked for Firefox are the following ones from nspr4.dll (naturally, we can use TrustDefender for this task :-).
As per the above documentation from Mozilla, if you have full control over PR_Read and PR_Write, you have full control over any Internet connection that Firefox is making, regardless of whether it is HTTP or HTTPS. It also doesn’t even matter whether it is a site with an EV-SSL certificate, as seen in the below image of a legitimate site with an authentic EV-SSL certificate.
So by hooking these functions, Zeus has full control over the session and can now inject any arbitrary HTML code into the browser whenever the bad guys want. Naturally they can see the full URL as well.
Please note that Zeus uses the same approach for hooking the Internet Explorer, however, since Internet Explorer uses different libraries for Internet connections, different DLL’s will be hooked.
However we want to make it clear that Zeus is not exploiting any particular vulnerability in Internet Explorer or Mozilla Firefox. It compromised the environment where the browsers operate and thus is able to get full control over the session.
The interesting thing we observed is that the majority of the new Zeus variants don’t inject HTML code into public websites, but rather only do this once a user has been successfully logged in to a specific site. They do this for various reasons and we will cover these in more detail in our next in-depth report. However, by doing this it means that you can’t see Zeus in action without a valid login, making detection extremely harder.
The following screenshot shows the new Zeus variant in action for a financial institution[2]:
<<screenshot available in the in-depth report>>
Windows Vista and Windows 7
One of the most disturbing features of this new Zeus variant is the fact that is capable of running not only on Windows XP, but also on Windows Vista and Windows 7 (we only checked 32 bit so far).
The big question was how they can do this despite of the hardened features of both operating systems.
Well first of all, when you execute the Zeus Trojan the Windows UAC does not kick in, meaning that the Zeus Trojan installer does not run with administrator privileges.
Although this in itself is a good thing as it means the Zeus Trojan cannot do any system-wide changes, the bad news is that Zeus still manages to infect the currently logged on user. The upside of being able to infect the machine without UAC outweighs the downside of only infecting the currently logged on user since that’s who they are targeting anyway.
The Zeus v2 Trojan takes this into account and will use random names for all events and semaphores … so that it can happily run multiple instances for multiple users on the same computer.
After we executed the Installer, the following registry entry is added to make sure that the Trojan runs when the computer is rebooted. Please note that this entry is in HKCU which means that this only applies to the current user and not for any other users of the computer.
This is different to older versions of the Zeus Trojan as they would install themselves in the Userinit value of the Winlogon key globally (HKLM – HKEY LOCAL MACHINE).
Another point to note is that the filename is random and will be different for every installation.
Thus it becomes apparent that to overcome the hardened features of Windows Vista and Windows 7, Zeus v2 was forced to use a different approach to compromise the current user as it does not have the permission to change global settings on these operating systems.
What is very, very disturbing and worrying is that the Zeus v2 Trojan can pretty much do everything it does with or without administrator rights. You would assume that all of the hard work that Microsoft has put in to protect you would pay off. You would assume that using a user without administrator right is more secure, right? Well, it doesn’t really appear so.
Windows XP – without administrator rights
In Windows Vista and Windows 7, all users run without administrator rights and the UAC kicks in if some administrative privileges are needed. Such a concept doesn’t exist in Windows XP and therefore you are much more locked down if you run as non-administrator.
If we run the Zeus v2 Trojan under Windows XP SP3 without admin rights, we noticed the similar Windows Security Alert when the Zeus v2 Trojan tries to install the SOCKS proxy, however this time there is no option to allow it (as we don’t have admin rights).
There is no option to allow this and therefore the SOCKS proxy functionality will not be available. Funnily enough this means that Windows XP users without admin rights are better protected as Vista or Windows 7 users who run without admin rights by default!
However as noted above, this doesn’t stop the Zeus v2 Trojan itself from working and it just means that the SOCKS proxy feature is not working. Everything else works fine… So after the above dialog box is closed and the user logs in to a website with HTML injection configuration, “usual” behaviour will kick in.
The following screenshots depict a user without administrator rights on a Windows XP SP3 machine. (the red circles highlight the injected HTML). Please also note that the SSL certificate and everything else is correct)
<<SCREENSHOTS AVAILABLE IN THE IN-DEPTH REPORT>>
Code Injection
Traditional versions of Zeus would inject themselves into the winlogon.exe process and spread from there (e.g. to svchost.exe, lsass.exe, services.exe). However, since the new versions of Zeus don’t run with administrator privileges, they cannot inject any code running as a different user (especially the SYSTEM account). Therefore the new Zeus v2 Trojan injects itself into the following processes ctfmon.exe, explorer.exe, rdpclip.exe, taskeng.exe, taskhost.exe and wscntfy.exe instead.
The reason for this change in approach is pretty simple – winlogon.exe is a SYSTEM process and without administrator privileges, the Trojan would not be allowed to inject anything, so the above alternative targets were chosen as they all run as the currently logged in user.
Since all these processes run as the currently logged on user and the Windows security settings allow the Zeus Trojan to modify the memory allocated by any of these applications, Zeus is now able to hook key windows functions (see earlier chapter about hooking) and inject its own code into the process, bypassing the hardening features of Windows Vista and Windows 7.
An important fact to know is that the process that will be started through the registry key above will terminate itself after it injects itself into the other processes, meaning you won’t be able to find a process running under the name of olews.exe.
Microsoft / Firefox Phishing Filter
One interesting addition is that the Zeus v2 Trojan will disable the Phishing Filter that is enabled by default in Internet Explorer 7 and later versions. The Zeus v2 Trojan does this simply by altering the registry setting HKCUSoftwareMicrosoftInternet ExplorerPhishingFilter to set the Enable and EnableV8 names to 0.
Firefox users are slightly better off as the Zeus v2 Trojan hasn’t yet figured out how to disable the Safebrowsing features of Firefox.
Interesting observations
<< available in the in-depth report >>
TrustDefender’s Approach to Zeus v2
TrustDefender’s Forensics Engine will immediately pick up all of the new Zeus v2 infections by default, and will protect you against the threat from a frontend (user-view) AND a backend point of view. TrustDefender enables financial institutions to deal with Zeus v2 on the server side through its real-time, risk-based Enterprise Server, and the TrustDefender Agent will successfully protect the end-user at home. No longer does a financial institution have to rely on the end user to do something, but rather they can mitigate and deal with the threat from their own backend systems and feed this information into existing systems including risk-engines, adaptive authentication suites and transaction monitoring tools etc.
How to detect that a system is compromised
Since the new variant of Zeus doesn’t use complex rootkit techniques, detection is relatively easy. Simply start the registry editor (regedit.exe) and check for an entry in the Run section of HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun.
The things to look out for are:
- Name looks like a GUID (such as {26014332-876A-668A-546A-2A9930E39482})
- Value is a filename in %USERDIR%Application Data<RANDOM DIR><RANDOM FILE> (such as “C:Documents and SettingssupportApplication DataKyniinyqypy.exe”)
How to remove Zeus v2
Removal of the Zeus v2 Trojan is also much easier since no complex rootkit techniques are used.
Simply locate the file that is being run from the above registry entry and delete the registry entry and the file. After a restart, your computer is clean. ![]()
[1] http://www.zdnet.com.au/microsoft-ie-use-falls-below-60-339302834.htm
[2] It wasn’t straightforward to provide a screenshot as the configuration of the Zeus Trojan would only inject HTML into the browser after a successful login.








I think I have this virus or at least a similar variant, it has some of the symptoms you mentioned above, eg it gave me a firewall option for explorer.exe which I of course (being a gullible idiot) accepted.
However there is nothing in the HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun. of the registry other than a “default” file for Adobe updater.
Any other ideas where I might find this irritating thing so I can kill it in a brutal manner?