1 Executive Summary
We have seen many different examples how improvements in the security landscape have forced the bad guys to change tactics and achieve their results via different, potentially less useful, methods.
A prime example is the introduction of UAC in Windows 7 together with the default user not running as administrator. This poses a tricky question for malware developers: Do I ask for elevation (UAC) and risk that users get suspicious, or do I do whatever I can without administration privileges?
Well the answer has been given. We’ve analysed Zeus before and Zeus will not bring up the UAC and will only infect the currently logged in user.
In this TrustDefender Labs report we look at a new strain of the notorious Torpig Trojan that gained massive publicity in 2008 when it was distributed together with the Mebroot / MBR virus. In this report we look at a new variant that will do an impressive amount of things completely without administrator privileges.
On a positive note, the lack of privileges restricts the trojan’s ability to hide itself deep in the system and is much easier to detect and remove.
2 Introduction
Torpig was basically the Zeus Trojan of 2008, as it was deployed as part of the Mebroot deployment vector. Its impressive feature list made it the Trojan of choice at that time.
We’ve covered Mebroot/Torpig back in 2008/2009; more details are on the TrustDefender blog here and here.
In the last few months, more and more Torpig Trojans appeared without the Mebroot component. It was pretty obvious that this was done to make Torpig work on newer operating systems such as Windows Vista and Windows 7 where the introduction of UAC and the removal of the admin-rights for the default user forced the Trojan writers to adapt.
Unfortunately these security improvements didn’t make the problem disappear; it only made their job harder.
So in essence, Torpig is still very impressive with the following features:
- Works perfectly fine in Windows 7
- No UAC
- Everything runs from usermode
- Browser hooking works nicely
- HTML web injection works like a treat
- Completely silent
However:
- It doesn’t feature any self-defences at all
- Torpig is visible as a process in task manager
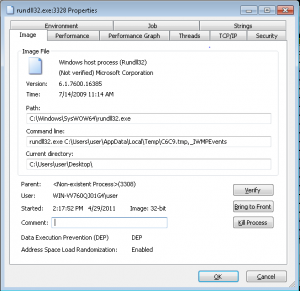
- E.g. rundll32.exe C:\DOCUME~1\support\LOCALS~1\Temp\1.tmp,_IWMPEvents
- Only current user is infected, not the whole machine
- If you kill that process, Torpig is disabled
- If you remove that file, Torpig is gone
- Other side effects: If IE runs as a separate user, Torpig will not be able to inject its HTML code anymore!
Other Trojans went down the same path. For Zeus 2+, the situation for example is as follows:
- No UAC appears
- Zeus runs as current logged in user
- Browser hooking still possible
BUT Zeus is also easily detectable, easily removable, and has almost no self-defences.
From Zeus 2.0.9.8 manual:
So let’s look at Torpig a bit more in detail as it employs a number of interesting techniques that are very similar, but also different to the Zeus/Spyeye/Gozi/Carberp’s of the world.
One of the main differentiating factors is how the HTML injection mechanism works, and obviously HTML injection is used quite heavily to attack bank websites.
Another interesting observation is that Torpig will hijack search results (e.g. Google) and most likely perform Clickjacking. This is something we noticed with Carberp as well and we believe that there is so much money to be made with this, it too important not to do it.
3 Installation
We looked mainly at the Torpig sample with MD5 of 70675a7053ae38adb77d70a056956684.
It was first seen on April 10, 2011.
- http://www.threatexpert.com/report.aspx?md5=70675a7053ae38adb77d70a056956684
- http://www.virustotal.com/file-scan/report.html?id=ff3def895115cbf489dad2ce98602c8acd4f8bf6bb591684c3c2d2e7254f93a0-1302476190
3.1 C&C DNS generation algorithm
One interesting fact is that while we installed the Trojan on April 10, even 2 months later it still successfully finds responding C&C servers that are up-and-running!
It achieves this by using an algorithm where Torpig will generate new domains daily to connect to on its quest to get access to a C&C server.
The fact that after 2 months our Torpig Trojan still finds responsive C&C servers says a lot about our current efforts in disrupting this infrastructure!
3.2 System modifications
As mentioned in the introduction, the main purpose of the Torpig Trojan is to also infect Windows Vista/7 machines, so even though we installed the Trojan on a Windows XP SP3 machine with full admin rights, the payload does exactly the same thing as if it was running as non-administrator. With one exception as it will add itself to the global Autostart registry to infect all users and not just the current one.
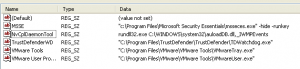
After the initial binary is executed, it will drop a DLL into the user’s temp directory and add the following command to the Autorun registry (only to HKCU – Current User):
rundll32.exe C:\DOCUME~1\support\LOCALS~1\Temp\1.tmp,_IWMPEvents
The interesting part is that they could have developed this as an executable, but then the Zeus executable would show up in the task manager. Using rundll32.exe (which is a legitimate Microsoft component) it can “hide” behind it.
The command above means that the system will load the 1.tmp DLL file and invokes a function call to the function _IWMPEvents.
3.2.1 It tries to infect the whole system, if possible
Even though the payload only affects the current user, Torpig will actually drop another DLL and tries to load this into the process with admin rights, if possible.
That means that if your user has administrator rights, all (!) users will be infected. If the user doesn’t have admin rights, only the current user is infected.
This is the Autorun in HKLM (Local Machine):
3.3 Code injection into other processes
As part of the installation, Torpig will inject executable code into other (system) components. Most notably into “explorer.exe”, which is a process that runs in the user’s context (no admin rights needed). Torpig did the same thing quite heavily before as well (back in 2008).
3.3.1 Basic user-mode rootkit techniques
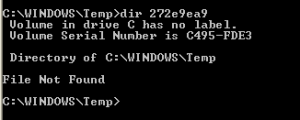
Torpig will employ some very basic usermode rootkit techniques, such as very limited file hiding techniques. For example, the Torpig code within the explorer.exe process will create a temporary file:
The file is hidden in the file system with a hooking of FindFirstFile/FindNextFile and won’t be visible in the Windows explorer. However the “old” tab-completion trick still works (just open a command prompt and let the tab auto-complete the filename).
3.3.2 Named pipe !mscom$
In the “old” days back in 2008, Mebroot and Torpig used named pipes quite extensively to enable the various components to communicate.
It almost surprised us to see that one of the named pipes is exactly the same (\\\\.\\pipe\\!mscom$). Also the protocol used for the communication is still the same with some extensions. Chapter 8 (Appendix A) is dedicated to the named pipe communication.
3.3.3 32 bit vs 64 bit
Torpig successfully installed and operated on 32 bit systems. It successfully installed on 64 bit systems as well, but it didn’t initialize properly (e.g., the named pipe !mscom$ wasn’t created).
However the DLL’s were dropped and loaded with rundll32.exe in almost exactly the same way.
3.4 Operating System / Brower compatibility
We tested various browsers and according to its technical capabilities, Torpig will work with Internet Explorer and Firefox. We see here the same improvements that we have seen with almost all other Trojans – that Torpig enhanced itself to work on Firefox due to its increased popularity.
However not all browser / OS seem to work. Here is the matrix:
- Windows XP, Vista, 32 bit
- Worked fine with IE 7,8
- Worked fine with Firefox 3.5 and 3.6. Didn’t work with Firefox 4 (!)
- Windows 7, 32 bit
- Didn’t work with IE 8 (!)
- Worked fine with Firefox 3.5 and 3.6. Didn’t work with Firefox 4 (!)
- Windows 7, 64 bit
- Didn’t work at all. Not even the named pipe was created
3.5 Logical components
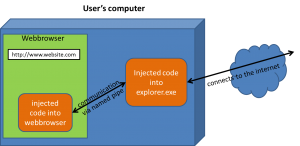
Torpig is made up of two main logical components.
The web browser code communicates with the explorer.exe code via the named pipe. The internet request then (e.g. to the C&C server) will be done from the explorer.exe process.
Note: It is pretty obvious that the fact that the internet requests are done by the explorer.exe process has numerous advantages. First of all, no browser plugins can see the traffic (as the traffic doesn’t occur in the browser), but also local firewalls and security solutions will not see anything.
3.6 C&C server communication
The C&C server communication is encrypted with a custom encryption mechanism and it looks pretty much unchanged from the one used before (described here: http://www.f-secure.com/weblog/archives/vb2008_kasslin_florio.pdf).
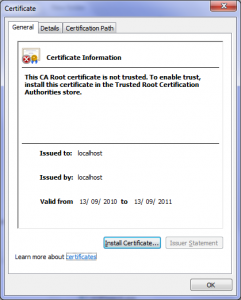
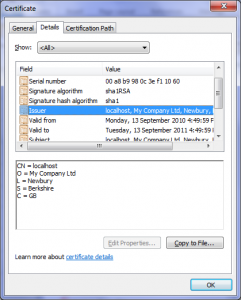
3.6.1 HTTPS Certificate
The requests to the C&C server are encrypted with SSL and a self-signed HTTPS certificate is used. This is possible due to the fact that the explorer.exe does the communication and “only” the content is then injected directly into the web browser’s process. So the web browser itself doesn’t even see any reference to the C&C server!
The following HTTPS certificate was used for the communication.
The “Valid from” date of 13 September 2010 surprised us a little bit as it is quite “old”…
3.6.2 The use of Geographic IP lookup
It seems that the C&C server quite heavily uses geo IP lookups to determine what should happen and whether a system should be infected or not. We successfully infected a machine in Australia, while we haven’t had such “luck” in the UK or Germany.
4 HTML content injection (MITB)
4.1 Browser hooking
Torpig uses the same mechanism as everybody else to hook the web browser process.
By hooking these functions, Torpig can get full control of the web browser traffic and can change whatever it wants. Please note that this also applies to HTTPS (EV-SSL) traffic.
4.2 Approach
Before we go into too much detail of how it works, let’s have a look at how Torpig uses the HTML content injection (Man-In-The-Browser).
First let’s be clear what we’re talking about. These instances below are examples of one particular configuration file of Torpig. All the examples we saw used a different approach for the HTML content injection than what we have seen in most Zeus/Spyeye configuration files.
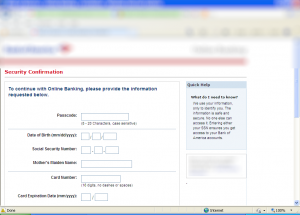
This particular sample will not show anything suspicious before the user actually provides his authentication credentials (including 2-Factor-Authentication code). Before this information is sent to the “real” banking server, Torpig will inject additional form fields to steal more data complementary to the stolen login credentials.
So in this sense, Torpig doesn’t even attack the authentication system as such, but rides at the back of the existing session.
After all the provided information is collected and sent to the C&C server, Torpig “simulates” a correct login by using JavaScript to POST the login information to the login server
4.2.1 Identity theft (MITB) examples
In this section we provide screenshots to various banking sites. The target list for the Torpig trojan can be found in the Appendix and in no way is this list exhaustive
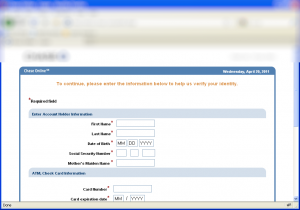
After logging in (with a fake account), the following screen appears:
Torpig’s configuration file checked every single entry to make sure it is correct. For example, it will check with Luhn’s algorithm whether the credit card number is actually a valid number!
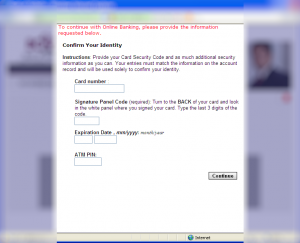
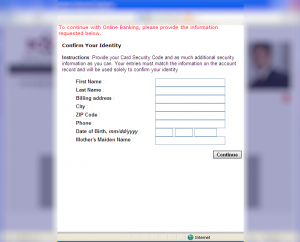
While in most cases, we have seen “just” one additional page injected; we also came across an example where multiple pages will be injected.
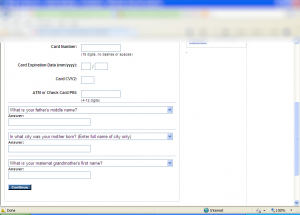
First, they ask for Card related info:
Then query identity related info:
Ok, so how does this work in detail?
4.3 HTML injection details
This 10 page section is only available in the full indepth report. Please request one from labs@trustdefender.com
4.3.1 Curiosities
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
4.3.2 Flaws in the system
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
4.4 Conclusion
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
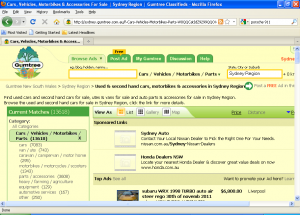
5 Hijacks search results (Clickjacking)
A more and more popular feature even for transactional banking Trojans are the hijacking of search results.
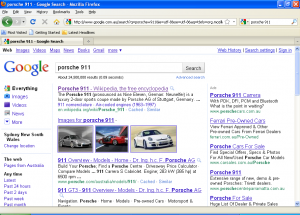
Let’s assume you search for “Porsche 911” in Google.
Clicking on the first link (which should get us to Wikipedia) will send us to the following page:
Oops??
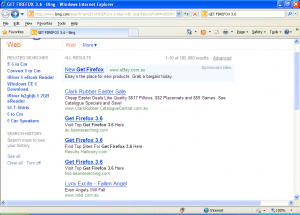
Another example: Searching for “Get Firefox 3.6” leads us to the following page…
Doesn’t look too good, that result page.
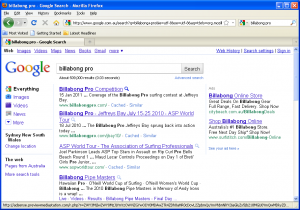
Another example: (check out the link in the status bar that will be invoked when clicking on the first hit)
6 Removal
Torpig can be fully removed by deleting the two files from the Autorun registry that are referenced from the following two locations:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, and
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Be sure to delete the right entry; in our case it was the entry with the rundll32.exe that references a .tmp file in a temp directory (Caution: be sure to know what you do in the registry editor as mis-usage could result.)
rundll32.exe C:\DOCUME~1\support\LOCALS~1\Temp\1.tmp,_IWMPEvents
Simply remove the two entries and delete the files from the hard drive.
Reboot the computer and you are clean.
7 TrustDefender
7.1 TDpro
Torpig uses the “usual” techniques to hook into the browser process. In addition to the code injection (executable and HTML) to the various components, one unique feature of Torpig is that the communication to the C&C server is done from the explorer.exe process. So even if there is a browser plugin or firewall checking all internet requests from the web browser, there is nothing to look at.
TrustDefender fully detects and protects users and enterprises from this threat, both on a process level (code injection), but also from the TCP/IP level (Secure Lockdown).
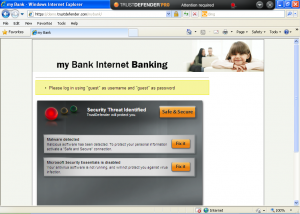
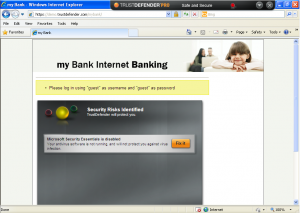
Below are a couple of screenshots from a walkthrough with TrustDefender with a demo site.
First it detects the malware.
And then the “Safe & Secure” mode will fully protect against it.
7.2 TDzero
As TrustDefender Zero utilizes our patent-pending page fingerprinting approach, it will detect the modifications to the page and therefore provide the financial institutions an early-detection system that doesn’t rely on blacklists, heuristics, updates or any downloads… It is completely transparent and an effective tool to protect against Man-In-The-Browser attacks of all sorts.
8 Appendix A: named pipe communication
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
8.1 Static target list output (same tool we used back in 2008)
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
8.2 Dynamic communication
This section is only available in the full indepth report. Please request one from labs@trustdefender.com
9 Appendix B: attached information to download
This section is only available in the full indepth report. Please request one from labs@trustdefender.com