As if the “old” mebroot trojan isn’t bad enough, the bad guys have released a new version of the highly successful e-banking trojan. And the bad news is that they changed a lot! Someone must have been busy over the last couple of months.
Basically the new version of Mebroot performs the same tasks and does the same badness as the previous versions that we have covered quite substantially on this blog before (see e.g. here and here).
However the big difference is that it is hiding in the system much much better as before to make sure
- it can infect your system without you knowing
- stay there as long as possible
To reiterate: Everything that was written how to detect mebroot is invalid and doesn’t apply anymore… No rg4sfay file in Windowstemp anymore, no reference to !win$… No detection with GMER’s special mbr.exe program and GMER itself only lists a couple of detached threads… Nothing really suspicious…
This new version also has the most exhaustive list of banking and broking websites we have seen – with virtually all major financial institutions in Australia, UK, USA, Spain, Italy, Germany and more. But also more and more non-bank websites are part of this list, like partycashier.com (the online payment from a popular poker site) and government sites like pay.gov (electronic payments to the US Govt). To find out whether your financial institution is affected, please do get in touch with us. (send an email to info@trustdefender.com)
Technical Details:
From a technical point of view, lots has changed in this version, however the core is still the same and Mebroot will inject itsself into services.exe which then holds also the configuration file and is in control of the updating process to the C&C server.
However everything is now encrypted. No plaintext files anymore with the captured details, no more plaintext internet requests. Everything is encrypted and most importantly all communication from the C&C server is encrypted as well. This effectively makes it impossible to sinkhole a mebroot C&C server. The mebroot trojan would immediately see that the connection is not from a genuine mebroot C&C server… Pretty clever…
In our case, two files were created in the c:WINDOWSTEMP folder, namely $$yt7.$$ and $$$dq3e. Both files are not visible in a directory listing and they hold the encrypted version of the stolen data.
The code injection into the browser processes is done as before through IAT hooks that TrustDefender’s Forensics Engine will pick up and the ‘Safe&Secure Mode’ will automatically protect the user by isolating the webbrowser’s process.
So again, all TrustDefender users and all financial institutions and enterprises who are employing the TrustDefender Enterprise Server are fully protected against this attack.
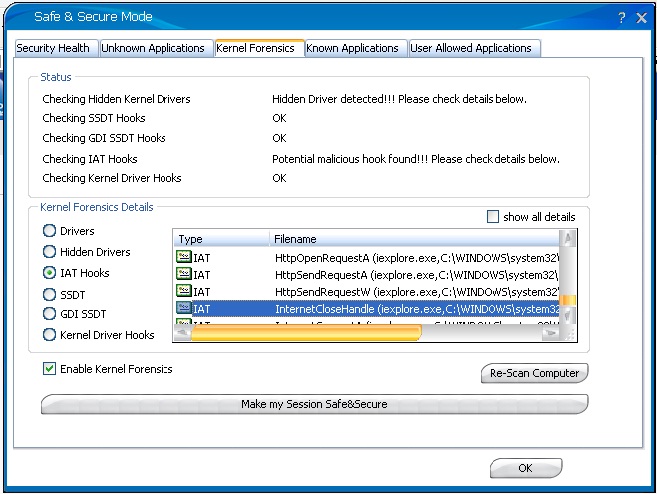
Thanks for this – this confirms an infection on the system I’m investigating.
This is the only site on the net covering the latest in Mebroot virus infections. I am also investigating a system that just got a Mebroot infection two days ago, and it’s extremely nasty. I’ve worked in IT and been hacking Windows internals for 15 years and just can’t believe how bad this one really is.
What are the removal steps for this latest iteration?
I am infected with the same virus. What shall one do??
Thanks
Lloyd